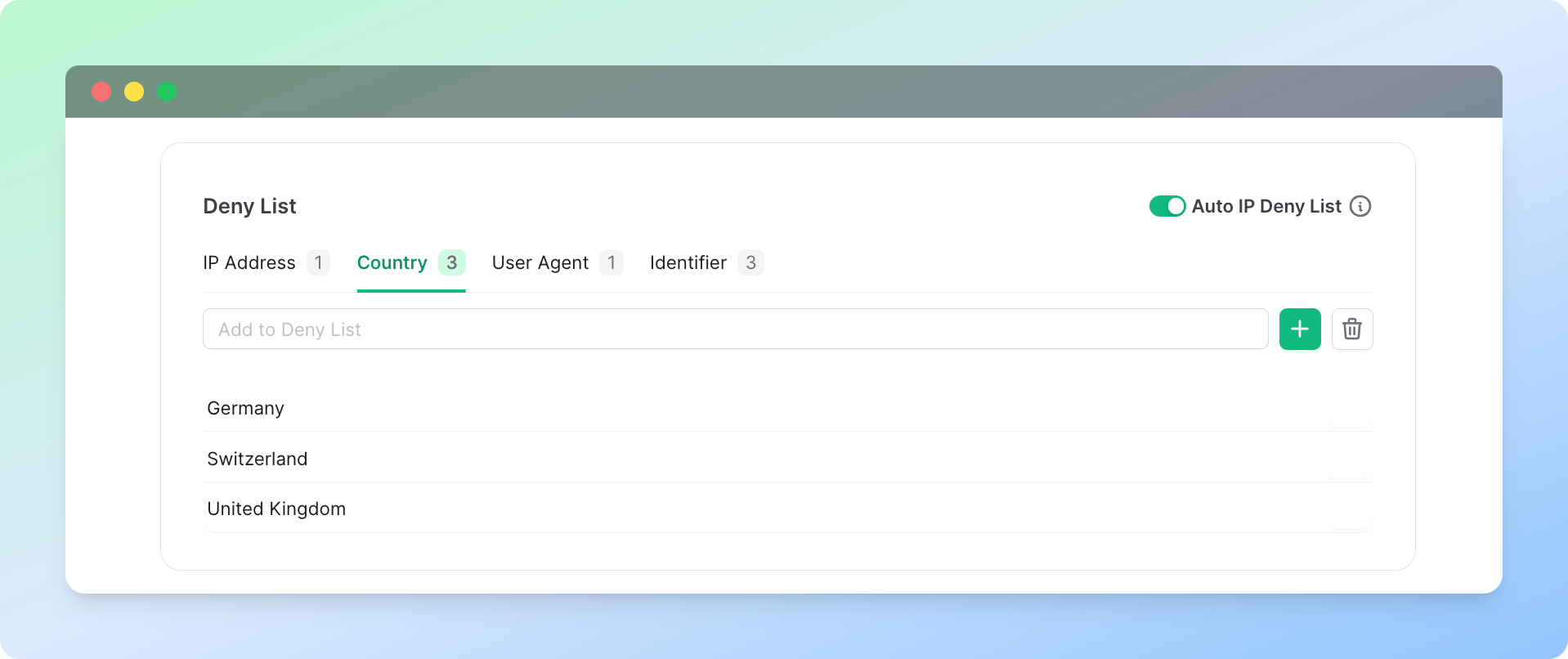
Deny List
Imagine that you want to block requests from certain countries or from some user agents. In this case, you can make use of deny lists introduced in ratelimit version 1.2.1. Deny lists allow you to block based on IP addresses, user agents, countries and identifiers. To enable checking the deny list in your Ratelimit client, simply passenableProtection as true:
limit is called, the client will check whether any of these values
are in the deny list and block the request if so.
reason field will
be "denyList". deniedValue will contain the value in the deny list.
See limit method
for more detailts.
Client also keeps a cache of denied values. When a value is found
in the deny list, the client stores this value in the cache. If this value
is encountered in the following requests, it is denied without calling
Redis at all. Items are stored in the cache for a minute. This means that if
you add a new value to the deny list, it will immediately take affect but when you
remove a value, it can take up to a minute for clients to start
accepting the value. This can significantly reduce the number of calls to Redis.
Contents of the deny lists are managed from the Ratelimit Dashboard.
You can use the dashboard to add items to the deny list or remove them.
If you have analytics enabled, you can also view the number of denied
requests per country/ip address/user agent/identifier on the dashboard.